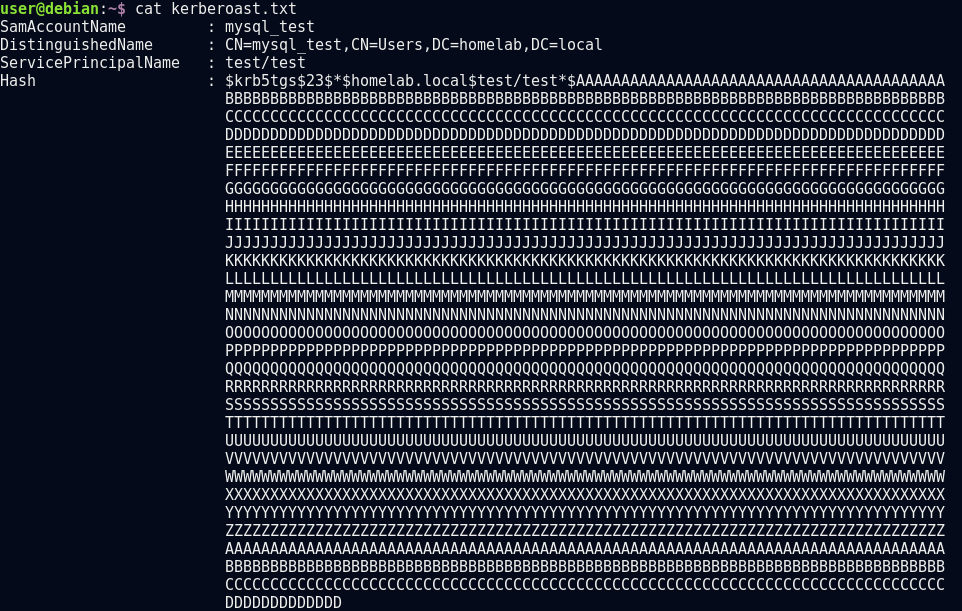
Today, I used SharpRoast from the released tool set which is a C# implementation of Kerberoasting and wrote a crappy bash one-liner that will parse the output into hashcat format for you to crack!
Kerberos
In a nutshell, Kerberos is used to authenticate to services on the Windows domain using a ticketing system. When a user authenticated to the domain wants to access a service, the user requests a service ticket from the domain controller. The domain controller does not control authentication to the service. This responsibility is given to the service itself. Once the user has a service ticket, it presents the ticket to the service and the service will determine if the user can access the service.
Kerberoasting is an attack on this authentication protocol. The service ticket granted by the domain controller is encrypted with the service account's NTLM hash (ding ding!). If we can crack the NTLM hash we can authenticate as the service account. This is important because service accounts generally have administrative access on the server providing the service. Based on the nature of service accounts, they can even be given administrative access to machines that interact with the service. All in all, compromising service accounts can give additional access that one previously didn't have leading to full compromise of a domain.
Some key things that make Kerberoasting so effective:
1. Any user on the domain can request these tickets.
2. You do not need to be a local admin on your machine.
3. Offline cracking so you don't have to worry about locking accounts out.
3. Offline cracking so you don't have to worry about locking accounts out.
3. People use shitty passwords.
SharpRoast
SharpRoast is a C# implementation of Kerberoasting released by harmj0y about a month ago!
The output of SharpRoast gives you the SamAccountName, DistinguishedName, ServicePrincipalName and the Hash (in hashcat cracking format). The only issue is the hash is broken across multiple lines with a ton of whitespace that you have to delete before you can throw it in your cracker.
Demo
This is an example of the output of a single hash from SharpRoast. Now imagine manually parsing multiple of these into one lined hashes! That'd be a nightmare.
I know this isn't the prettiest or most efficient way to do this, but hey it works! Here's the one-liner:
cat kerberoast.txt | grep Hash -A 29 | sed 's/\<Hash\>//g' | sed s/://g | sed s/--//g | sed -r 's/\s+//g' | tr '\n' ' ' | sed 's/\s//g' | sed 's/$k\{1,\}/\'$'\n&/g' > kerb_hashes_hashcat.txt
Some shortcomings:
2. The part where you 'grep Hash -A 29', 29 lines may truncate or capture too many lines depending on your ServicePrincipalName and DistinguishedName. Play around with this number to make sure you're capturing the entire hash.
And just like that you're ready to fire up your cracker and hopefully crack the hashes for some plaintext passwords :)
Thanks for reading! Hope you learned a little something about Kerberoasting and how it can be used to further your access on a Windows domain. If you spot any errors, please let me know on twitter or by email!